1. Bad moon rising
Barely halfway through 2014, the year's already poised to become the scariest yet for digital security—topping even 2013's massive Target breach.
We’ve seen hacks against big-name retailers like eBay, Michael’s, and
Neiman Marcus—plus hotels, online forums, and numerous other websites.
The current tally of compromised credit cards from major breaches is
closing in on 5 million, and online accounts?—half a billion.
Beyond active attacks, go-to encryption tool TrueCrypt was lost, and we've suffered through the single biggest web security lapse ever. As we close in on the halfway point for 2014, here are the 10 biggest security stories so far.
Beyond active attacks, go-to encryption tool TrueCrypt was lost, and we've suffered through the single biggest web security lapse ever. As we close in on the halfway point for 2014, here are the 10 biggest security stories so far.
2. Heartbleed bleeds the web
Thousands of major websites worldwide
scrambled in April after a nasty little flaw turned up in OpenSSL—a
widespread tool for securing online communications, including HTTPS
websites. Dubbed Heartbleed,
this devastating bug threatened to expose usernames and passwords, user
data, and even the SSL keys sites use to securely identify themselves.
The problem was widespread: affected sites included Instagram, Netflix,
and Tumblr.
Although it was a serious flaw, Heartbleed also inspired several major tech companies to fund poorly-supported open source projects. The first group to receive assistance—surprise!—was the OpenSSL Software Foundation.
Although it was a serious flaw, Heartbleed also inspired several major tech companies to fund poorly-supported open source projects. The first group to receive assistance—surprise!—was the OpenSSL Software Foundation.
3. TrueCrypt shuts up shop
In May, customers were shocked to be
suddenly rerouted from the TrueCrypt encryption software's website to
the project’s SourceForge page. There, they found this message:
“WARNING: Using TrueCrypt is not secure as it may contain unfixed
security issues.”
At first, it looked like a hoax or a hack, because TrueCrypt's advice to switch to Microsoft’s closed-source BitLocker encryption tool was diametrically opposed to the project's ideals. Several weeks later, however, TrueCrypt’s demise appears to be real. There are attempts to resurrect the project under new management, even as rumors about hidden Latin messages from TrueCrypt's developers swirl.
At first, it looked like a hoax or a hack, because TrueCrypt's advice to switch to Microsoft’s closed-source BitLocker encryption tool was diametrically opposed to the project's ideals. Several weeks later, however, TrueCrypt’s demise appears to be real. There are attempts to resurrect the project under new management, even as rumors about hidden Latin messages from TrueCrypt's developers swirl.
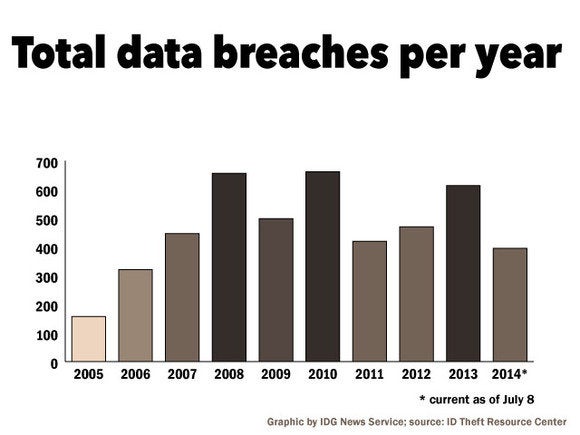
4. Breaches, breaches, and more breaches
A security review wouldn’t be complete without a roundup of major data breaches. EBay is
the most notable victim: In May, the site announced a devastating data
breach that included names, email and home addresses, phone numbers,
dates of birth, and encrypted passwords. Reports put the number of
affected users around 145 million.
Hobby retailer Michael’s joined eBay in the data breach Hall of Shame, along with AOL, Avast's online forums, Holiday Inn and Marriott Hotels, and Neiman Marcus. Restaurant chain P.F. Chang’s recently announced it was also investigating a data breach. And oh yeah, another 360 million usernames and passwords surfaced on hacker forums in February. Ugh.
Hobby retailer Michael’s joined eBay in the data breach Hall of Shame, along with AOL, Avast's online forums, Holiday Inn and Marriott Hotels, and Neiman Marcus. Restaurant chain P.F. Chang’s recently announced it was also investigating a data breach. And oh yeah, another 360 million usernames and passwords surfaced on hacker forums in February. Ugh.
5. La Oops
But sometimes, a breach deserves individual recognition—like the hack that Seagate-owned LaCie
announced in April. The hard drive and peripheral storage maker said
its online storefront had endured a whopping year-long data heist from
March 27, 2013 to March 10, 2014. LaCie said it wasn’t sure what kind of
data had been pilfered, but it may have included customer names, email
addresses, credit card numbers, and card expiration dates. Crazy.
6. Ransom goes rampant
If 2013 was the year of the personal data breach, then 2014 is shaping up to be the year of digital hostages and ransomware.
Malicious software that threatens to ruin your PC if you don’t pay a
certain amount of money is an old game, but hackers upped the stakes in
the early part of 2014. In late May, iOS users around the world woke up
to find their iDevices locked via Apple's Find My iPhone service, with hackers demanding money to restore them. Then in June, security firm ESET found the first example of file-encrypting ransomware on Android. Sites like project-management web app Basecamp were also held ransom unless they paid up to stop distributed denial of service (DDoS) attacks.
7. GnuTu Fail
Heartbleed wasn’t the only significant SSL/TLS bug in 2014. In February and March, both Apple and the Linux community
were scrambling to fix flaws in their implementations of online
security protocols. In Apple’s case, someone had mistakenly included an
extra 'goto fail' programming statement that left encrypted data sent
via SSL/TLS open to capture by hackers.
In the Linux case, the GnuTLS library had a programming flaw exposing user data to potential breaches, similar to Apple’s 'goto fail' problem. In the case of GnuTLS, however, it’s suspected the programming flaw existed for as long as 10 years—prompting Linux community leaders to say, “Huh, Gnu knew?” ( Groan —Ed.)
In the Linux case, the GnuTLS library had a programming flaw exposing user data to potential breaches, similar to Apple’s 'goto fail' problem. In the case of GnuTLS, however, it’s suspected the programming flaw existed for as long as 10 years—prompting Linux community leaders to say, “Huh, Gnu knew?” ( Groan —Ed.)
8. Pliable crypto-currency
Bitcoin security hit a road bump in February: A flaw dubbed “transaction malleability” led to attacks against several Bitcoin exchanges, according to Bitcoin news site Coindesk.
The flaw could theoretically allow an attacker to substitute a phony
transaction for the original one, thus redirecting Bitcoins from the
intended recipient to the attacker.
Transaction malleability was serious enough that it was an early theory as to why embattled Bitcoin exchange Mt. Gox closed its doors. Mt. Gox’s problems were later revealed to go deeper than a software bug, however, and a fix addressing transaction malleability was issued in March.
Transaction malleability was serious enough that it was an early theory as to why embattled Bitcoin exchange Mt. Gox closed its doors. Mt. Gox’s problems were later revealed to go deeper than a software bug, however, and a fix addressing transaction malleability was issued in March.
9. Outlook snoop
Government agents aren’t the only snoops
who might be plundering your Outlook.com inbox. Microsoft might also
take a peek…at least if you’re up to no good. In March, Microsoft
‘fessed that it snooped on the personal email of
both a blogger and a former employee, seeking evidence that the
employee was leaking proprietary company information to the blogger. (To
its credit, Microsoft revamped its privacy policy after the backlash.)
The case highlights how American digital due-process is woefully inadequate. After all, private emails sitting on third-party servers should be considered just as private as those love letters stashed in the back of your closet.
The case highlights how American digital due-process is woefully inadequate. After all, private emails sitting on third-party servers should be considered just as private as those love letters stashed in the back of your closet.
10. Gameover for Gameover botnet
Two positive stories offer some hope.
In June, a global law-enforcement coalition temporarily disrupted a nasty botnet called Gameover ZeuS. Infected Windows PCs were harvested for personal data and also used to distribute Cryptolocker ransomware.
Gameover includes a peer-to-peer component, as well as online proxy servers and strong encryption, according to Krebs on Security. Gameover affects an estimated 500,000 to one million PCs worldwide, and the disruption—dubbed ‘Operation Tovar’—only served as a chance to clean up infected PCs. U.S authorities indicted Evgeniy Mikhailovich Bogachev, 30, of Anapa, Russia, on several criminal charges related to operating the botnet.
In June, a global law-enforcement coalition temporarily disrupted a nasty botnet called Gameover ZeuS. Infected Windows PCs were harvested for personal data and also used to distribute Cryptolocker ransomware.
Gameover includes a peer-to-peer component, as well as online proxy servers and strong encryption, according to Krebs on Security. Gameover affects an estimated 500,000 to one million PCs worldwide, and the disruption—dubbed ‘Operation Tovar’—only served as a chance to clean up infected PCs. U.S authorities indicted Evgeniy Mikhailovich Bogachev, 30, of Anapa, Russia, on several criminal charges related to operating the botnet.
11. Google's end-to-end revenge
Revenge is a dish best served cold, and
Google made sure its vengeance pie was well and truly cooled before
serving it up to the National Security Agency. As the fallout over Edward Snowden's NSA revelations continues,
Google announced it wanted to make end-to-end encryption for webmail
easier to use with a new Chrome extension. Called End-to-End,
the extension is currently in a public alpha phase and not yet ready
for wide release. When it goes live, however, it will be one of several
new projects promising to keep your most private emails secure from
prying eyes and snooping government agencies.